WebLinkCSI enables you to safely inspect weblinks from emails, etc., before attempting to open them.
WebLinkCSI enables you to safely inspect weblinks from emails, etc., before attempting to open them.
We all have received a link in an email or been curious about the potential danger of a link. WebLinkCSI (Web Link Communications Security Inspector) was designed for just that type of curiosity. WebLinkCSI will inspect the communication utilized in URIs. This inspection is done without sacrificing privacy and endpoint security. It is portable, so you can load it on a flash drive, keeping you safe even when away from your desktop machine.
WebLinkCSI features a simplistic UI that keeps the focus on the data it provides. Each URI element found in the web link you supply is inspected, and the analysis output is sectioned off between a set of horizontal lines in the output. WebLinkCSI is a useful asset for anyone that wants to keep informed regarding a link before committing to opening.
The analysis output format of each section is:
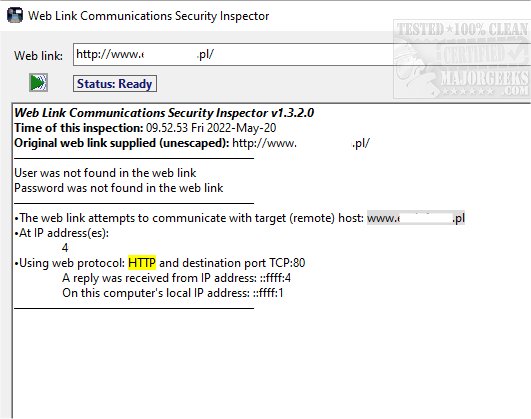
The target host (name or IP address) with which the URI element tries to communicate
The IP addresses of the target host, if the target is identified as a name in the link
The web protocol, either HTTP or HTTPS, and port number on the target host. Http connections are displayed in yellow to indicate that this URI element communicates using the insecure protocol
The result of a simple connection test to the target host over the TCP port is shown in the web link. If the target replies, the replying IP address from the target and the receiving IP address on your client computer are returned
On a successful reply where a communication element uses ‘HTTPS,’ a standard anonymous client-server protocol negotiation is conducted, then the analysis further provides:
The session encryption handshake protocol is used to set up communication. Where the agreed-upon encryption protocol is considered weak, the weak protocol used will be
highlighted yellow.
The MAC hashing algorithm is used to preserve integrity in the communication stream through qualities of messaging secrecy
The datastream cipher is used to encrypt the payload data being transmitted between you
and the target host
The public certificate data from the target host is returned under ‘•Target host certificate identity information.’ All values returned here are useful in assessing security. Still, the subject and issuing entity properties can quickly look at the target’s identity to see if this is an organization (or country) you expect or trust. The elements in the certificate authority chain are also returned so that you can inspect each element and assess the trust of the certificate chain.
Similar:
What's the Best Antivirus and Is Windows Defender Good Enough
How-To Use the Google Chrome Malware Scanner & Cleanup Tool
How to Always Show Full Address or URL in Mozilla Firefox
How to Always Show Full Address or URL in Google Chrome
How to Report Online Scams, Spam Emails and More
Download