Well, not entirely. They aim to add the click to play tweak aimed at curbing scourge of drive-by website attacks that is already in use with most Chrome browsers on tablets.
Michael Coates, Director of Security Assurance, posted to heis latest blog.
Is it a band-aid approach? Yes. Meaning it doesn't fix the underlying flaws, but it is a good idea for preventing the more and more prevalent "drive by" infections by requiring user interaction. Plus it gives us all another good reason to look forward to HTML5.
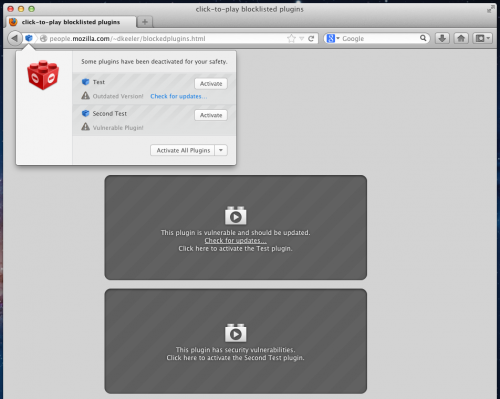
Firefox intends to block Java, Reader, and Silverlight based content.
Michael Coates, Director of Security Assurance, posted to heis latest blog.
One of the most common exploitation vectors against users is drive by exploitation of vulnerable plugins. In this kind of attack, a user with outdated or vulnerable plugins installed in their browser can be infected with malware simply by browsing to any site that contains a plugin exploit kit. We’ve observed plugin exploit kits to be present on both malicious websites and also otherwise completely legitimate websites that have been compromised and are unknowingly infecting visitors with malware. In these situations the website doesn’t have any legitimate use of the plugin other than exploiting the user’s vulnerable plugin to install malware on the their machine. The Click to Play feature protects users in these scenarios since plugins are not automatically loaded simply by visiting a website.
Is it a band-aid approach? Yes. Meaning it doesn't fix the underlying flaws, but it is a good idea for preventing the more and more prevalent "drive by" infections by requiring user interaction. Plus it gives us all another good reason to look forward to HTML5.

Firefox intends to block Java, Reader, and Silverlight based content.

