Emsisoft Decryptor for Ziggy will decrypt files held by the Ziggy ransomware.
Emsisoft Decryptor for Ziggy will decrypt files held by the Ziggy ransomware.
This particular ransomware's admins have shut down and offered up the keys publicly; however, it is always advisable to use a decryptor not associated with the threat actor for obvious reasons, as well as being a little wary of anything provided by the said threat actor. So, because of this, Emsisoft released their own decryptor for use.
The Ziggy ransomware first appeared near the end of 2020. It works by encrypting files using RSA-4096 and AES-256 GCM, and adds the extension ".id=[].email=[].ziggy".
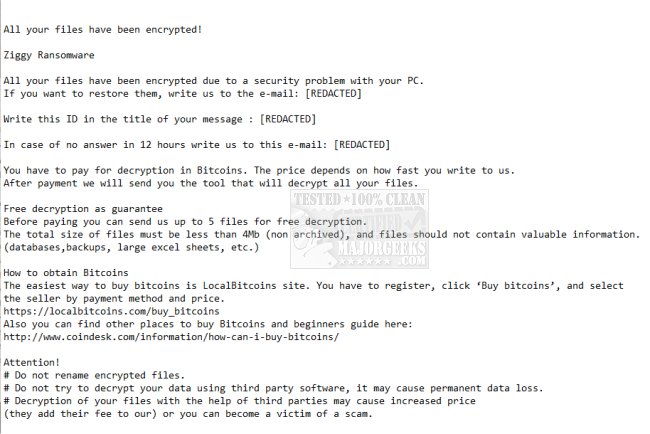
The ransom note executable "## HOW TO DECRYPT ##.exe" displays the following message:
The decryptor will display the reconstructed encryption details once the recovery process has finished. The display is purely informational to confirm that the required encryption details have been found. Once a key is found, click OK to open the primary decryptor user interface.
Emsisoft Decryptor for Ziggy pre-populates the locations to decrypt with the currently connected drives and network drives. Additional locations can be added via the Add button.
After adding all the locations you want to decrypt to the list, hit the Decrypt button. This will start the decryption process. The screen will switch to a status view, informing you about your files' current process and decryption status.
Emsisoft Decryptor for Ziggy will inform you that the decryption process is complete. If you require a report for your records, you can save it by clicking the Save Log button. You also have the option to copy it straight to your clipboard for use in emails, forum posts, etc., if needed.
Similar:
Which Anti-Malware App Is Best and Can It Run Alongside My Antivirus
What's the Best Antivirus and Is Windows Defender Good Enough?
How to Tell the Difference Between a Virus and a False Positive
What to Do When Your Norton or McAfee Antivirus Expire
Download