Emsisoft Decryptor for Aurora can help to decrypt files held hostage by the Aurora ransomware family.
Emsisoft Decryptor for Aurora can help to decrypt files held hostage by the Aurora ransomware family.
Aurora is a ransomware family that encrypts files using XTEA and RSA. Aurora may also be known as "Zorro", "Desu", or "AnimusLocker". Known extensions include ".Aurora", ".aurora", ".animus", ".ONI", ".Nano", and ".cryptoid".
The Aurora malware leaves many ransom notes; examples include "!-GET_MY_FILES-!.txt," "#RECOVERY-PC#.txt," and "@_RESTORE-FILES_@.txt."
Here is an example of the note's contents:
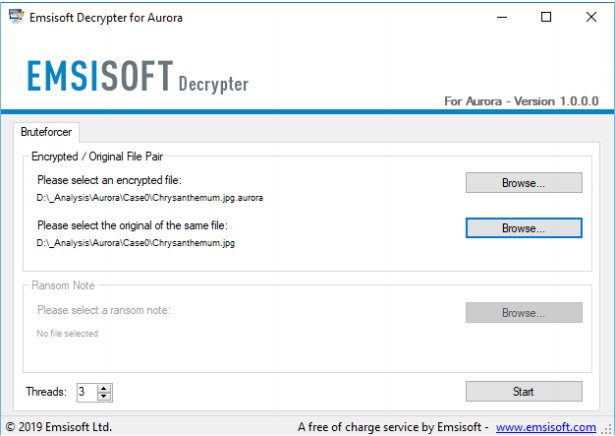
The decryptor requires access to a file pair consisting of one encrypted file and the original, unencrypted version of the encrypted file to reconstruct the encryption keys needed to decrypt the rest of your data. Please do not change the original and encrypted files' file names, as the decrypter may perform file name comparisons to determine the correct file extension used for encrypted files on your system.
To use Emsisoft Decryptor for Aurora, run the decrypter as an administrator; on the next window, you will select the pertinent info and then click the Start button. The decryptor will then begin to reconstruct the required encryption parameters. Depending on the ransomware and your computer, this process can take a significant amount of time.
Upon completing the reconstruction, Emsisoft Decryptor for Aurora will display the reconstructed encryption details once the recovery process has finished.
Decryptors typically offer various options depending on the particular malware family. The available options are located in the Options tab and can be enabled or disabled there.
After adding all the locations, you want to decrypt to the list, click the Decrypt button to start the decryption process. The screen will switch to a status view, informing you about your files' current process and decryption status.
Emsisoft Decryptor for Aurora will notify you that the decryption process is complete. If you require a report for your records, you can save it by clicking the Save Log button. You also have the option to copy it straight to your clipboard for use in emails, forum posts, etc., if needed.
Similar:
Which Anti-Malware App Is Best and Can It Run Alongside My Antivirus
What's the Best Antivirus and Is Windows Defender Good Enough?
How to Tell the Difference Between a Virus and a False Positive
What to Do When Your Norton or McAfee Antivirus Expire
Download