Emsisoft Decrypter for HKCrypt decrypts files encrypted by the HKCrypt (AKA Hacked Ransomware).
Download
Emsisoft Decrypter for HKCrypt decrypts files encrypted by the HKCrypt (AKA Hacked Ransomware).
HKCrypt first showed up in late 2017. It encrypts a victim's files using the RC4 algorithm, then adds the extension ".hacked" to files. This nasty little bit of malware pretends to be running a Windows update to fool you, then shows a lock screen requiring that you contact "payment.hkdecrypt @ mail.ru."
This ransomware also leaves several ransom notes in English (@readme_English.txt or How_to_decrypt_files.txt), Spanish (@Readme_Spanish.txt), and Italian (@Leggimi_decrypt_Italian.txt).
The English ransom note contains the following text:
It is important that you remove the malware from your system first. Otherwise, it will repeatedly lock your system or encrypt files.
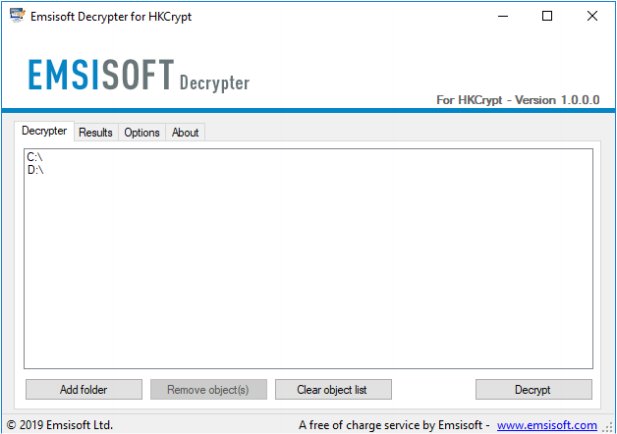
By default, Emsisoft Decrypter for HKCrypt will pre-populate the locations to decrypt with the currently connected drives and network drives. Additional locations can be added using the Add button.
Decrypters typically offer various options depending on the particular malware family. The available options are located in the Options tab and can be enabled or disabled there.
After you have added all the locations you want to decrypt to the list, click the Decrypt button to start the decryption process. The screen will switch to a status view, informing you about the current process and decryption status of your files.
Emsisoft Decrypter for HKCrypt will notify you that the decryption process is complete. If you require a report for your records, you can save it by clicking the Save log button. You also have the option to copy it straight to your clipboard for use in emails, forum posts, etc., if needed.

Download

