AccessChk allows administrators to see what kind of accesses specific users or groups have to resources including files, directories, Registry keys, global objects and Windows services.
AccessChk allows administrators to see what kind of access specific users or groups have to resources, including files, directories, Registry keys, global objects, and Windows services.
AccessChk uses Windows Powershell and must be run from a command prompt. It is geared towards system admins and IT techs and should be run from the proper directory. If not, then all commands must start with a period and backslash, for example, ".accesschk" or ".accesschk64"
The authors link at the top of this page has all the available commands, but just in case, here they are:
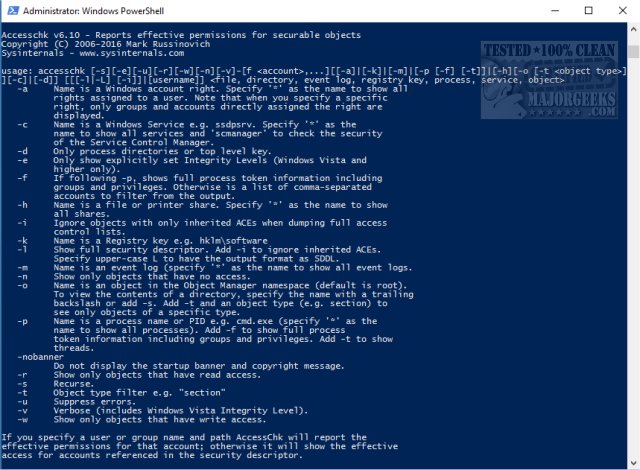
-a Name is a Windows account, right. Specify "*" as the name to show all rights assigned to a user. Note that only groups and accounts directly assigned to the right are displayed when you specify a specific right.
-c Name is a Windows Service, i.e., ssdpsrv. Specify "*" as the name to show all services and "scmanager" to check the security of the Service Control Manager.
-d Only process directories or top-level keys
-e Only show explicitly set-Integrity Levels (Windows Vista Vista and higher only)
-f If following -p, shows full process token information including groups and privileges. Otherwise is a list of comma-separated accounts to filter from the output.
-h Name is a file or printer share. Specify '*' as the name to show all shares.
-i Ignore objects with only inherited ACEs when dumping full access control lists.
-k Name is a Registry key, i.e., hklmsoftware
-l Show full security descriptor. Add -i to ignore inherited ACEs.
-n Show only objects that have no access
-o Name is an object in the Object Manager namespace (default is root). To view the contents of a directory, specify the name with a trailing backslash or add -s. Add -t and an object type (i.e., section) to see only objects of a specific type.
-p Name is a process name or PID, i.e., cmd.exe (specify "*" as the name to show all processes). Add -f to show full process token information, including groups and privileges. Add -t to show threads.
-q Omit Banner
-r Show only objects that have read access
-s Recurse
-t Object type filter, e.g. "section"
-u Suppress errors
-v Verbose (includes Windows Vista Integrity Level)
-w Show only objects containing write access
Download